SSTP is one of the technologies used to establish a VPN tunnel, such as PPTP or L2TP. Since SSTP traffic goes through SSL (Port 443), which is the same protocol as HTTPS uses, it's most likely the SSTP packets can be transported through most of public network like;hotels, airports, libraries and so on.
That's a big advantage to deploy SSTP.
SSTP uses a SSL certificate. You can purchase a cert from third party like Verisign or GoDaddy, or you can use one signed by Active Directory Certificate Authority.
I decided to create one with AD CA, since our VPN clients are all domain users/computers.
I'd like to share my experiences about deploying SSTP here.
SSTP deployment involves these steps;
- Built and set up AD CA (Please see my other post (8021.X Wireless Authentication Part1)
- Create a SSL certificate template on CA (Explain in this article, part1)
- Issue a SSL certificate from the SSTP server(Explain in this article, part1)
- Install RRAS on the SSTP server (Part2)
- Configure SSTP on the SSTP server (Part2)
- Deploy the sSTP VPN settings to clients (Part3)
The environment in this scenario:
- Windows 2008 R2 AD CA, Enterprise CA
- Windows 2012 R2 SSTP server, 2 NICs, NIC A and NIC B
The prerequisites:
- Configured NIC A & B with private IP addresses in the same subnets
- A doesn't have DNS nor Default GW configured
- The SSTP server is located behind the firewall. The Firewall has NAT configured so that SSL packets sent to the SSTP server's public IP will be forwarded to NIC A of the SSTP server
- Registered the A record of the SSTP server with the public DNS
- VPN clients will access the SSTP server using a host name not an IP. the host name must be resolved publicly
Create a SSL Certificate Template on AD CA
- Open the Certification Authority Console
- Expand the Certification Authority --> the CA server --> Right-click on the Certificate Templates
- Locate IPSec (Ver8.1) and right-click --> Select Duplicate Template
-
Select Windows Server 2008 Enterprise
Click OK -
Properties of New template will open
Configure the following tabs and click OK - Right-click on the Certificate Templates --> Select New --> Certificate Template to Issue
General: Template display name and Template name
Request Handling: Check off Allow private key to be exported
Extension: Select Application Policies --> Click Edit --> Add --> Server Certification
Subject Name: Check off Supply in the request
Issue a SSL Certificate from the SSTP Server
- Log on to the SSL server
-
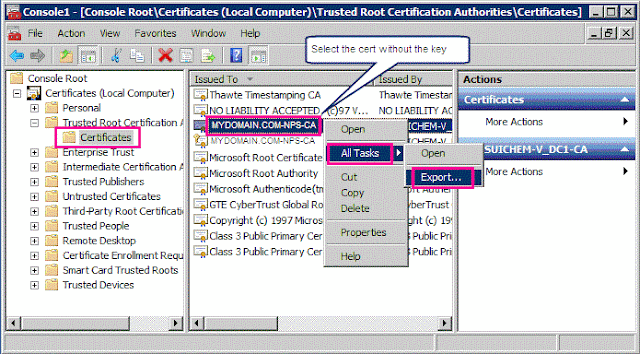
Open the Certificate console
Expand Personal --> Certificates
Right-click and select All Tasks --> Request New certificate... -
The Certificate Enrollment window will open
Click Next twice -
Check off Show all tmplates
Scroll down and find the certificate template created in the previous steps
Click Details
Click Properties - On the Subject tab add Subject name and Alternative name as following
- Click Enroll
<Subject name>
Type: Select Common name
Value: Type the SSTP server's FQDN Ex.) RemoteAccess.myDomain.local
<Alternative name>
Type: Select DNS
Value: Type the SSTP server's A record host name Ex.) vpn.myDomain.com
Type: Select IP address (Ver4)
Value: Type the SSTP server's A record public IP address
*Clients use the host name specified as DNS alternative Subject name when they connect to the SSTP server. Thus, this is very important that the SSL certificate has either the publicly routable hostname as a subject name or the SSL server's public IP address.
Of course, you can have both of them.
The SSL certificate must have correct SANs otherwise clients end up with a certificate error. Setting up VPN on RRAS is simple. I think certificate part is the most complicated and not so many system administrators know exactly what to do including myself. I hope this article helps you.
I will explain the RRAS configuration in the Part2.