DC - Create Wireless Group, Group Policies
CA - Install and Create Enterprise Certificate Authority
NPS - Install NPS, Add RADIUS client, Create 802.1X Wireless Policy
Back in October, our 5-year-old BlusSocket Wireless Controller went down suddenly and never came back to life. We needed a replacement within two weeks because we expected about ten guests to visit our office for several important meetings. Our vendor recommended and implemented Aruba 620. This was a good opportunity for me to tighten up the wireless netowrk security.
Our old wireless network used WPA-Personal, which requires the both of client machine and controller to have the same preset passphrase. Any computers, devices and users could access the wireless LAN with the passphrase.
There are many security holes in this mechanism.
I decided to implement 802.1x authentication, which requires different components such as DC, CA, NPS and Group Policy and complecated to deploy but it's worth the cost.
Once you have 802.1X authentication, whenever an eligible domain user logs in a domain computer, he/she automatically connects to the wireless network.
To accomplish 802.1X, you need Domain Contoller, CA (Certificate Authority) and NPS (Network Policy Service). These three roles can be installed on one server.
1. Create a WirelessUsesr group to apply 802.1X Wireless NPS Policy and XP Wireless Network Group Policy
In DC, create Wireless Security group and add users
Give Wireless group an Apply Group Policy Permission
2. Install Active Directory Certificate Service
In any domain member server, install the Certificate Authority role, which is a part of Active Directory Certificate Service role
In this case, this is the first enterprise CA.
In this case, this is the first enterprise CA.
3. In DC, Modify the Default Domain Group Policy so that client computers install the certificate automatically
4. In any domain member server, Install Network Policy Service
Add Network Policy and Access Services role à Network Policy Service.
5. Create a RADIUS client
6. Create and Configure 802.1X Wireless Policy
Add Aruba (RADIUS Client) created in the step 5
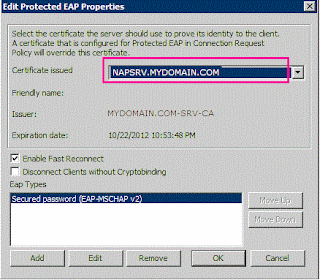
Select "Microsoft: Protected EAP (PEAP)"
Select the NPS certificate, which should be like YourNPSServerName.YourDomain.COM Click Configure...
Select the group created in the step1
Click Next in Configure Traffic Controls
Click Finish
Check the newly-created Secure Wireless Connection policy
You can change the configuration from the properties
Corresponding Connection Request policy has been created automatically
Continue to Part 2